Platform
Leader in offensive cybersecurity
Vulnerability prioritization
Identify and prioritize your most recent vulnerabilities, especially those exploited in the wild, impacting your assets exposed on the Internet, with the feature “trending attacks”.
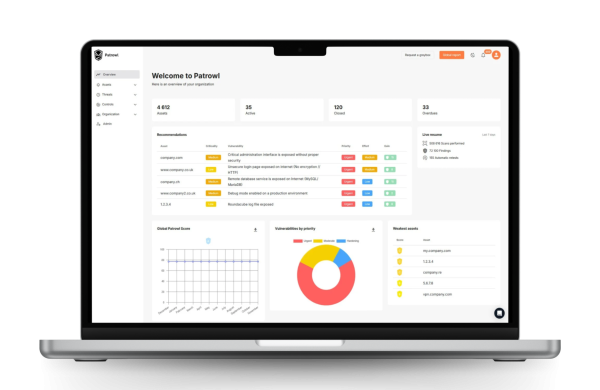
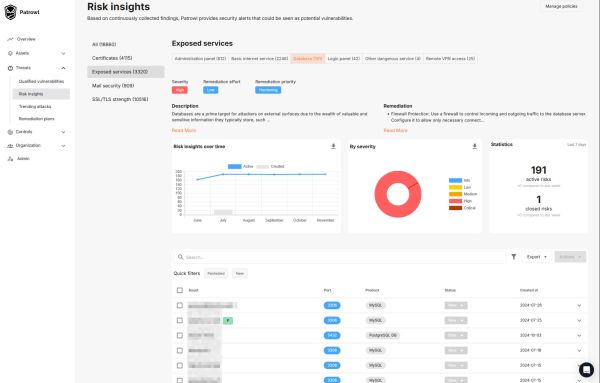
Bad practices and compliance with Risk Insights
With continuous discovery, Patrowl will identify your bad practices shown as use cases: my certificates, my exposed services, my domains...
These are not vulnerabilities, rather hardening or compliance issues and this can result in a security incident or a bad scoring/rating solution score.

Known and Unknown Vulnerabilities
With the continuous penetration test, Patrowl will identify:
Known vulnerabilities (CVE and non-CVE referenced)
Unknown vulnerabilities (OWASP, 0days)
These qualified and proven vulnerabilities are presented with their level of criticality, a proof of concept and a remediation plan.
Their criticality means that they must be managed quickly.
Vulnerabilities actively exploited in the wild
The trending attacks feature will let you know if your assets are impacted or not by vulnerabilities exploited in the wild.
As a CERT (Computer Emergency Response Team), Patrowl performs continuous and real-time threat monitoring. The sources of this CTI monitoring include CERT FR advisories, the CISA list of vulnerabilities exploited in the wild (KEV / Known Exploited Vulnerabilities), vendors' alerts, researchers' blogs, code repositories, microblogging platforms, etc.
When a new exploit code is detected or a vulnerability is exploited in the wild, Patrowl is informed and, having a quasi-exhaustive repository of what you expose on the Internet, very quickly checks the vulnerability on all your assets exposed on the Internet.
If the asset is pentested, then the qualification will be safe, telling you whether it is impacted or not. If it is only mapped, Patrowl will identify the risk as potential. As a result, three cases arise:
Impacted: your asset is impacted by a vulnerability exploited in the wild by cybercriminals. It is imperative to take the alert into account as soon as possible
Warning: your asset is only mapped and it is potentially impacted by a vulnerability exploited in the wild
Not impacted: if nothing has been found and no exploit code is available, you are not at risk and you are informed
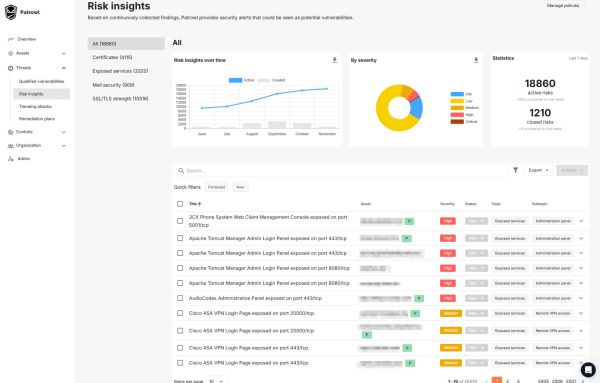
Continuous monitoring of emerging threats
Patrowl's Trending Attacks category lists the latest massively reported and exploited vulnerabilities that could impact your assets. These vulnerabilities come from the KEV catalog published online by CISA (USA) or CERT alerts (France), and are constantly updated to facilitate your cyber watch.
For every new trending attack identified, Patrowl tests your assets placed under pentest and automatically transforms the threat into a vulnerability if you are impacted.
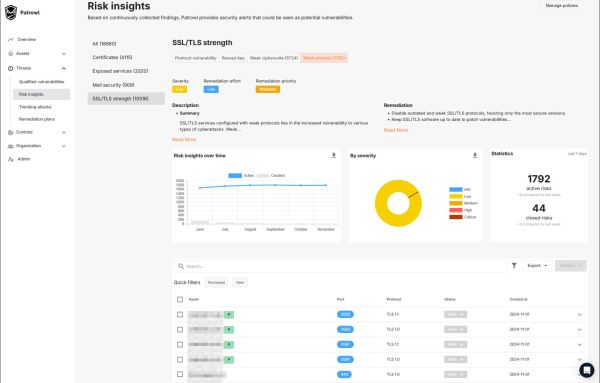
Real-time alerts on cyberthreats








