Platform
16 January 2024 CVE Vlad
2024 for 2 weeks and already 7 vulnerabilities actively exploited

Ce contenu vous plait
Partagez-le sur les réseaux
This year unfortunately kicks off with several critical vulnerabilities, known as CVEs, actively exploited by opportunistic attackers, as well as for targeted attacks. In less than 2 weeks, there are already 7 vulnerabilities massively exploited.
The security checks were implemented in Patrowl last week for Ivanti, Gitlab and Juniper, and in 2023 for Joomla and SharePoint.
The CISA (U.S. defense agency) has referenced all these vulnerabilities in its 'Known Exploited Vulnerabilities Catalog,' meaning the list of vulnerabilities actively exploited by attackers: https://www.cisa.gov/known-exploited-vulnerabilities-catalog.
Ivanti Connect Secure VPN
If you have remote access (VPN) based on the Ivanti Connect Secure VPN solution (formerly Pulse Secure and Juniper Secure Access), I strongly recommend checking the version of your equipment, updating it, and investigating if you haven't been compromised.
On January 10th, the vendor issued an advisory regarding 2 vulnerabilities that, combined, allow taking control of your remote access gateways:
- CVE-2023-46805, authentication bypass
- CVE-2024-21887, command injection on the VPN web portal with administrator rights
The vulnerabilities have been detected as actively exploited, so it is VERY strongly recommended to investigate. In the article below, you will find some indicators (IoCs) to identify a potential compromise:
They also provide Yara detection rules and IoCs in CSV format.
Interestingly, Circl published an opinion on the subject with their thoughts on these devices: It’s almost heartwarming to see our supplier finally roll out security patches, albeit at a pace that would embarrass a snail. In the meantime, while we wait with bated breath, this could be an excellent moment to ponder whether our current VPN provider is a champion of cybersecurity or just a champion of testing our patience.https://circl.lu/pub/tr-78/
They publicly state what everyone has been saying for years. These devices have changed little since Juniper (except for the product name). They are an assembly (among other things) of insecure open-source technologies (or poorly assembled 😉), with web interfaces far from standard, lots of historical CGI files...
Unfortunately, all of this is assembled without modern security (sandboxing, jails, containerization, SELinux...). To their credit, all these features come from customer requests that they had to add (download the VPN client, have a purely web VPN without client software to install, strong multi-factor authentication...)
As soon as someone looks into it, it ends with vulnerabilities: https://thinkloveshare.com/hacking/failed02_pulse_secure_vpn_guacamole_websocket_hooking/ and https://www.youtube.com/watch?v=0ayQl2oB1tA .
Since the patch is not yet available (scheduled for January 22), there is a workaround to apply if needed: https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways.
Circl also recommends disabling the remote access service 😂.
Gitlab
Gitlab is one of the most well-known and widely used development and continuous integration tools.
A critical vulnerability was identified by a researcher (as part of a bug bounty program). This one, referenced CVE-2023-7028, simply allows resetting the password of a user account by having the reset link sent to the user's email. This works only if the user has not activated multi-factor authentication (MFA).
https://about.gitlab.com/releases/2024/01/11/critical-security-release-gitlab-16-7-2-released/
Unfortunately, the exploit is quite simple. In the password reset request, just put the user's email field twice: the legitimate one in the first and the attacker's in the second.
In image:
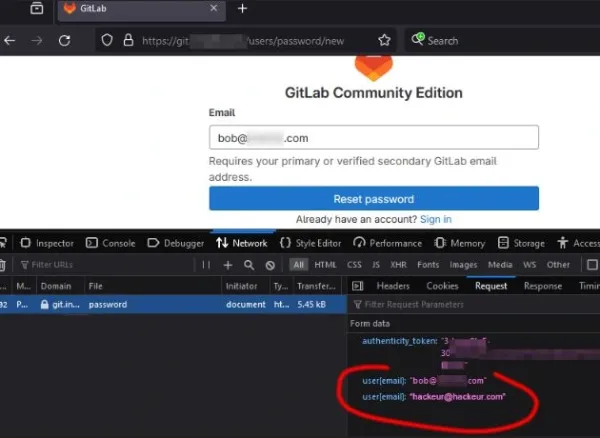
In raw data: &user%5Bemail%5D%5B%5D=bob%40**.com&user%5Bemail%5D%5B%5D=hacker%40hacker.com In raw "decoded" data: &user[email]=bob@**.com&user[email]=hacker@hacker.com
This vulnerability affects all GitLab families: Community Edition (CE) and Enterprise Edition (EE). https://about.gitlab.com/releases/2024/01/11/critical-security-release-gitlab-16-7-2-released/#account-takeover-via-password-reset-without-user-interactions
Since the vulnerability announcement, it is actively exploited in the wild by opportunistic attackers. GitLab offers a patch, so:
- Update https://about.gitlab.com/releases/2024/01/11/critical-security-release-gitlab-16-7-2-released/
- Investigate to see if an account has not been compromised (check password resets for accounts without MFA since early January, on 01/11 if you are confident 😉)
- Activate MFA for your users (if not already done).
Joomla
Joomla is a content management tool for creating websites, much like WordPress. A critical vulnerability has been identified, referenced: CVE-2023-23752.
It allows accessing the Joomla API without authentication, obtaining information about the configuration, and in some cases, the administrator's password. This vulnerability affects Joomla versions 4.0.0 to 4.2.7: https://developer.joomla.org/security-centre/894-20230201-core-improper-access-check-in-webservice-endpoints.html
So:
- Update to 4.2.8
- Investigate to see if the vulnerability has been exploited (check API access logs... if you have any)
- If in doubt, change the administrator's password
- Do not expose the Joomla administration portal on Internet!!!
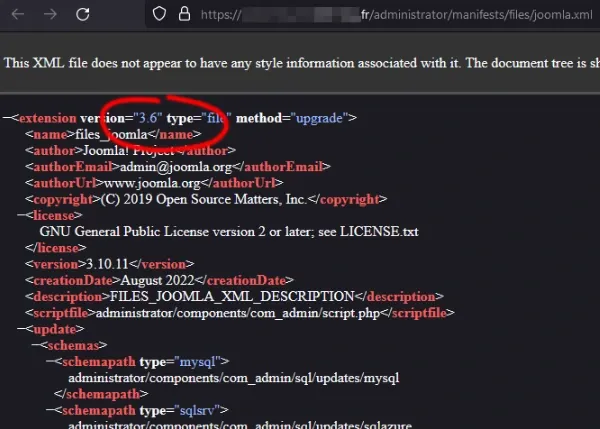
If you want to check your Joomla version, use this URL (replacing it with your site): https://mywebsite.com/administrator/manifests/files/joomla.xml
Juniper
Juniper, jealous of all these critical vulnerabilities, has just published a security bulletin concerning a vulnerability allowing its "EX series" routers and "SRX series" firewalls to be remotely controlled without authentication: This issue is caused by use of an insecure function allowing an attacker to overwrite arbitrary memory
This vulnerability is referenced as CVE-2024-21591 (with a CVSS criticality rating of 9.8/10) and is located in the "J-Web access" web component, which is the graphical interface to Juniper Web Device Manager. What a surprise...
Repeat after me: I NEVER expose an administration portal on the Internet!
Update quickly, or at the very least, restrict access to J-Web to trusted networks only.
Are there many J-Webs exposed on the Internet?
Quite a few... nearly 40,000 referenced in Shodan (with a simple query, I didn't try to optimize) :
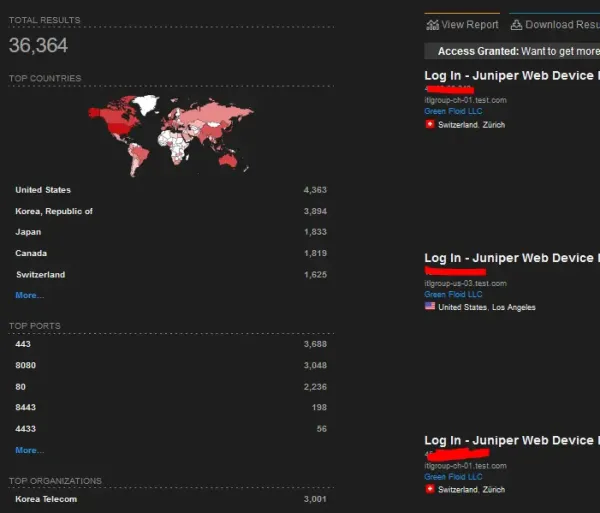
My research: https://www.shodan.io/search?query=title%3A%22Log+In+-+Juniper+Web+Device+Manager%22
You can also target specific versions with the icon: https://www.shodan.io/search?query=title%3A%22Juniper%22+http.favicon.hash%3A2141724739
You can vary with the version contained in the page body: SRX345-DC, SRX110H2-VA, SRX300 ...
Here's an example of J-Web in action:
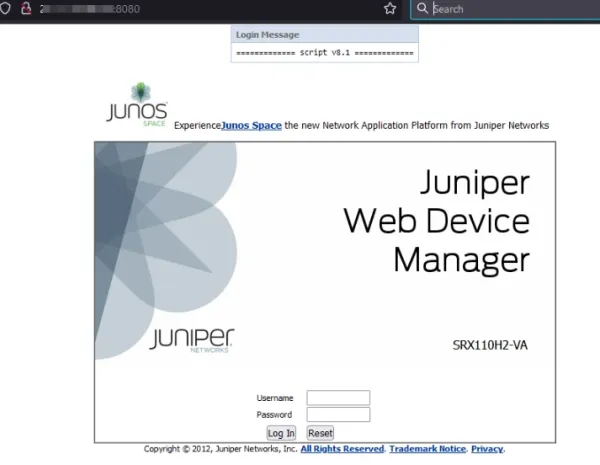
And if by chance, it has been misconfigured, maybe the default authentication works 😉: https://dariusfreamon.wordpress.com/2013/12/29/juniper-web-device-manager-default-admin-credentials/
The last one but not the least, Microsoft SharePoint
We talked about it last Tuesday during the OSSIR vigil: a complete exploit code was published a few weeks ago concerning vulnerabilities CVE-2023-29357 (authentication bypass) and CVE-2023-24955 (.Net code injection allowing functions such as System.Diagnostics.Process.Start() to be called, giving the possibility of executing malware if you want 😅 ).
These affect Microsoft SharePoint and had been announced at the March 2023 Pwn2Own competition in Vancouver.
Microsoft released patches in September 2023 "but", at first glance, not everyone has updated and for the past few weeks they have been actively exploited in the wild to take control of SharePoint servers. https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2023-24955
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2023-29357
The vulnerability is also listed by CISA in its list of the most exploited vulnerabilities in the wild: https://www.cisa.gov/news-events/alerts/2024/01/10/cisa-adds-one-known-exploited-vulnerability-catalog
The PoC of the exploit code: https://gist.github.com/testanull/dac6029d306147e6cc8dce9424d09868
Good luck 😉





