Platform
N°1 Offensive security as a service
CAASM
Identify exposures and vulnerabilities across your entire external attack surface with Cyber Asset Attack Surface Management.
The 100% French SaaS that automates time-consuming tasks, alerts you to critical vulnerabilities (0 false positives) and offers you a pragmatic remediation plan, with the option of retesting your corrections in just 1 click.
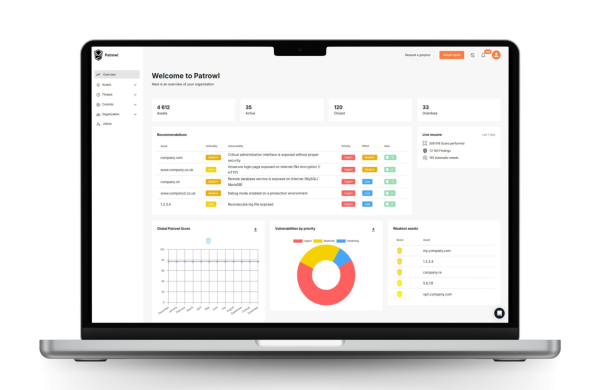
How CAASM works ?
At Patrowl, managing your external attack surface is based on a simple, effective and continuous method for identifying and eliminating vulnerabilities before they are exploited.
Mapping: Identify your exposed assets, including those forgotten or hidden (Shadow IT).
Identification: Detect critical assets and vulnerabilities on an ongoing basis with tools such as CART, PTaaS and CTI.
Remediation: Prioritize vulnerabilities and integrate management directly into your ITSM tools.
Control: Automate remediation follow-up and re-launch a retest in a single click if necessary.
What is Cyber Asset Attack Surface Management (CAASM) ?
In cybersecurity, knowing what you're protecting is the first line of defense. But with the proliferation of digital assets - applications, servers, cloud services - how can we be sure that none of them fly under the radar? That's where Digital Asset Attack Surface Management (DASAM) comes in.
The principle? Total visibility of all your digital and physical assets exposed to the Internet or other networks.
Our key features
80% automated penetration testing, with 20% verification by our experienced, certified penetration testers
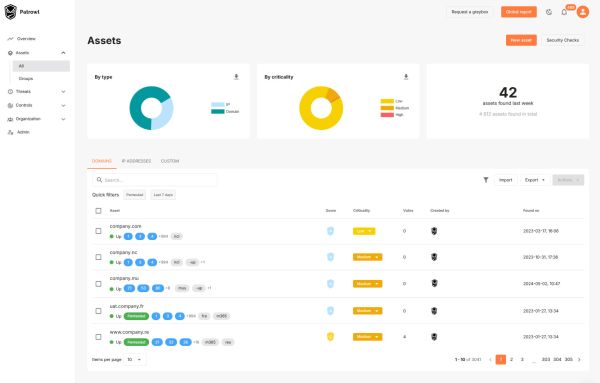
Map and control your exposed assets
Continuous detection of unknown assets: Reveal parts of your digital environment that you didn't even know were exposed, thanks to constant monitoring of your attack surface.
Proactive change management: Be informed immediately of any additions or changes to your digital assets, be they new services, IP addresses or recently deployed applications.

Identify vulnerabilities with precision
In-depth vulnerability analysis: Detect not only known vulnerabilities (referenced in databases such as CVE), but also those that are more subtle or specific to your context.
Continuous risk assessment: Prioritize what really counts: critical vulnerabilities with a direct impact on your operations or data, based on technical (CVSS, EPSS) and business scores.
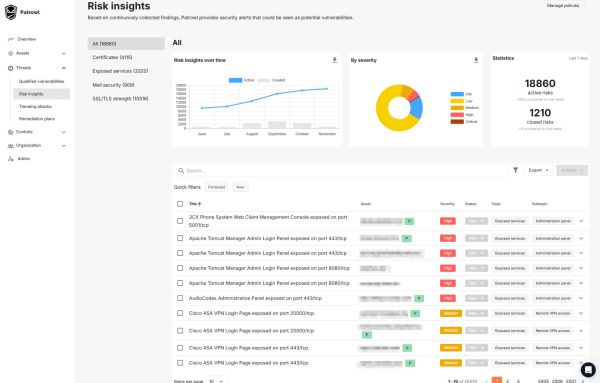
Maintain global control of your security
Centralized monitoring: keep track of your security controls across all your assets:
Security of exposed services (DNS, e-mail, SSL/TLS)
Integrity of certificates and sensitive configurations
Robustness of web applications and network practices
Proactive identification of misconfigurations: Locate structural vulnerabilities (default authentication, code injection, misconfigurations, etc.) before they are exploited.
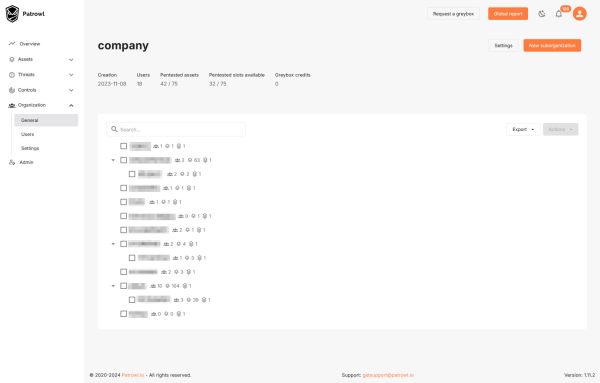
Simplified management and efficient collaboration
1-click reporting: Export your results as PDF, CSV or JSON directly from the dashboard.
Alerts and notifications: Stay informed of new threats via e-mail, Slack, Teams or your ticketing system (ITSM).
Multi-tenant solution: Manage multiple entities with distinct users, assets and groups tailored to your organizational needs.
ITSM integration: Synchronize your assets with your ITSM tools (Service Now, Jira, GLPI) for smooth tracking and rigorous control.




Asset types supported by Patrowl
IP addresses and subnets
Autonomous systems (ASN)
DNS zones and domain names (including second-level)
Critical DNS records: MX, SPF, DMARC, NS, etc.
FQDN (Fully Qualified Domain Name) and URLs
Tenants and accounts in the public cloud
Business e-mail addresses
Customized keywords: company names, brands, products, chemical formulas, etc.

Patrowl: An agile solution for proactive, optimized cybersecurity.
Loss of visibility for assets exposed on the Internet?
Do you lack visibility of your assets exposed to the Internet? With Patrowl, identify your assets in real time and reduce your external attack surface with our External Attack Surface Management (EASM) and Pentest as a Service (PTaaS). We also detect Shadow IT, phishing sites and counterfeiting.
Difficulty keeping up with new threats and vulnerabilities
Receive real-time alerts on vulnerabilities and threats to your exposed assets, both known and new. Apply prioritized remediation plans to act before attackers do.
Recruitment problems in cybersecurity?
Let Patrowl take care of time-consuming tasks thanks to its hyper-automation. Your team will be able to concentrate on remediation and high value-added actions.
Insufficient budget or budget cut?
Reduce your costs with a single, predictable platform. Replace external penetration tests, vulnerability scans and other services for an average ROI of 287%.
BENEFITS
Why Patrowl.io?
0 false positive
for qualified alerts
Simplicity
Saas without maintenance or client-side programming
0 setup
with fast, simplified commissioning averaging 30 minutes
24/7/365
Including secure access (encryption and MFA or SSO authentication)
100 %
Customer renewal rate in 2024.
"Faster than attackers"
Mentioned on Wavestone's radar
Winners of the Assises de la Cybersécurité innovation awards in 2022 and 2023
France Cyber Security” label.

Compliance and penetration testing
Patrowl simplifies adherence to security standards by ensuring regulatory compliance, helping you demonstrate the robustness of your cybersecurity posture. Here are the regulations it covers
DORA compliance
Regulation on digital resilience for the financial sector (banking, insurance)
NIS 2
European directive to protect critical infrastructures (energy, health, transport).
Cyberscore
Security note for digital services (websites, social networks).
Programme CaRe
Program to strengthen the cyber resilience of SMEs (industry, healthcare).

How does CAASM differ from other technologies?
CAASM differs from other technologies in several ways:
ASM monitors an organization's digital footprint to reduce its attack surface, while CAASM manages digital assets and analyzes internal and external vulnerabilities.
EASM focuses on external assets (websites, servers), while CAASM covers both internal and external assets for a complete view. EASM solutions are simpler to deploy.
CAASM manages shared assets and data, while DRP protects sensitive digital assets.
Who is CAASM for?
All companies exhibiting services on the Internet
Companies with many websites: Guarantee that all your domains, sub-domains and associated infrastructures are secure and up-to-date.
Multi-cloud organizations: Secure your public cloud tenants and prevent misconfigurations.
Sensitive brands and products: Monitor and protect your digital assets linked to brands, products or patents.
Companies with complex infrastructures: Maintain an overview of your IPs, ASNs and DNS zones to avoid blind spots.
CAASM use cases
If your organization has an extensive digital presence, such as websites, servers, cloud services or even brands to protect, Patrowl offers advanced External Attack Surface Management (EASM). The aim: to identify and secure all points of exposure, even those you might have overlooked.
What types of assets can be secured with Patrowl?
IP addresses and subnets: Protect your exposed network infrastructures and identify potential vulnerabilities.
Autonomous systems (ASN): Monitor the IP blocks allocated to your organization.
DNS zones and domain names: Ensure that all your domain names, DNS zones and sub-domains (even forgotten ones) are secure.
Specific DNS records: Patrowl manages and monitors all your critical DNS records, such as MX, SPF, DMARC and NS, to prevent spoofing or misconfiguration attacks.
FQDN and URLs: Identify all your fully qualified URLs or domain names that could expose insecure or obsolete services.
Cloud accounts and e-mail: Protect your public cloud tenants, corporate accounts and e-mail addresses from attacks targeting your sensitive digital assets.
Keywords and trademarks: Monitor your company names, trademarks, product names or even specific elements such as chemical formulas for misuse or accidental exposure.






