Platform
What is Cyber Threat Intelligence?
Threat Intelligence, or Cyber Threat Intelligence (CTI), is like having a network of spies monitoring your environment to protect your resources.
These spies discreetly collect information on potential threat actors: who they are, what weapons they intend to use, and where they will attack from.
With this information, you can anticipate attacks, reinforce defenses where necessary and better protect your systems.

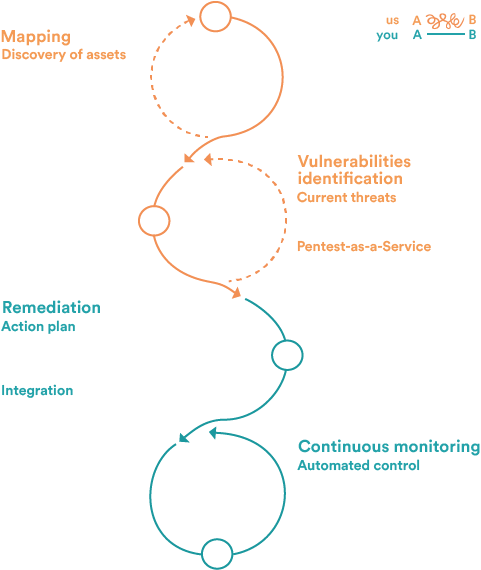
The stages of cyber threat intelligence with Patrowl
Patrowl offers a unique approach, combining proactive vulnerability management with automated penetration testing, so that you can concentrate on remediation.
Mapping of exposed assets
Identification and prioritization of vulnerabilities
Detailed remediation plans with one-click patches
Continuous monitoring: regular automatic tests, one-click retests...
The combination of automation and human expertise ensures reliable, actionable results, without unnecessary overload. Patrowl makes cybersecurity simple, proactive and effective!
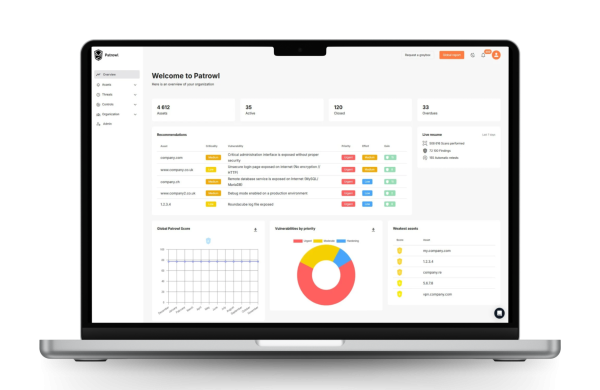
Platform and tool for Cyber threat Intelligence
Patrowl continuously protects you against emerging threats by combining detection, automation and remediation in an intuitive and streamlined SaaS solution, giving you better visibility of your assets and enabling you to prioritize the most critical vulnerabilities that could affect your business.
Features associated with Patrowl cyber threat intelligence
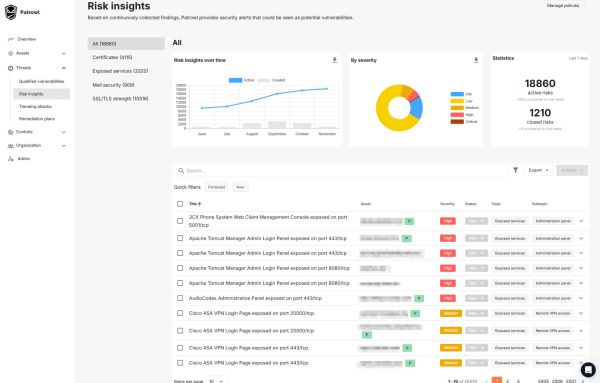
Identify your bad configurations
Patrowl's Risk Insight feature provides in-depth analysis of your exposed assets to identify vulnerabilities before they are exploited. This functionality covers:
✔ Certificate security: Detection of expired certificates, obsolete cryptography and risky protocols.
✔ Web application security: Audit of WAF/CDN protections and analysis of their effectiveness against cyberattacks.
✔ Messaging and credentials: Audit of email configurations, detection of password leaks and analysis of compromised databases.
✔ Exposed services: Identification of open ports and misconfigured services to limit unauthorized access.
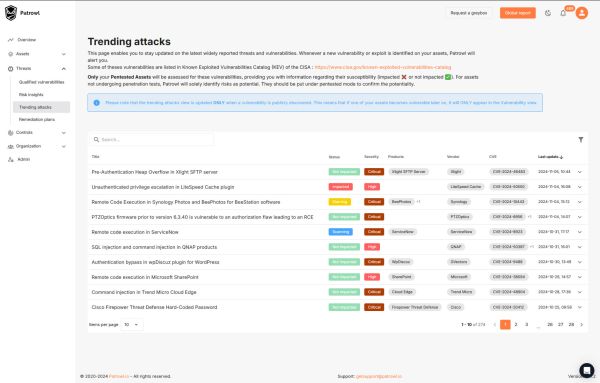
Anticiper les menaces avant qu'elles ne frappent
Trending Attacks feature from Patrowl offers continuous monitoring of actively exploited vulnerabilities. By leveraging databases such as KEV (Known Exploited Vulnerabilities) from CISA and CERT alerts, Patrowl:
✔ Prioritizes vulnerabilities based on their real impact.
✔ Performs automated tests on your assets to identify exploitable flaws.
✔ Sends real-time alerts as soon as an attack is detected.
This approach allows you to act before cybercriminals can exploit a vulnerability, thereby reducing the risk of compromise.

A proactive threat intelligence to stay informed.
Instead of wasting time manually searching for vulnerabilities in your components, Patrowl alerts you in real time about:
✔ Newly disclosed vulnerabilities (CVE).
✔ Unlisted flaws and misconfigurations (OWASP).
✔ Threats directly impacting your organization.
This allows you to anticipate attacks before they are exploited by cybercriminals.
Hyper-automation of repetitive tasks
Security teams are often overwhelmed with time-consuming tasks. With Patrowl, you can automate:
✔ The identification and prioritization of vulnerabilities.
✔ The management of alerts and security reports.
✔ The continuous execution of security tests and audits.
This allows SOC and IT teams to focus on remediation and strengthening the organization’s defenses.




Additional technical information
Certifications of our pentesters
Our experts are certified with advanced training:
SANS GIAC (GPEN, GWAPT, GXPN): Certifications for cybersecurity specialists.
OSCP: Offensive Security Certified Professional.
OSWE: Offensive Security Web Expert.
Security Testing Standards
Patrowl relies on recognized standards to ensure the quality of its assessments:
PTES: Penetration Testing Execution Standard.
OWASP: Web application security best practices.
SANS: Security auditing framework.
GDPR: Data protection compliance.
ANSSI SDE NP: Recommendations from the French National Cybersecurity Agency.
Assets Protected and Detected by Patrowl
Patrowl secures your exposed assets on the Internet before they can be exploited:
Network & IP: IPv4, subnets.
DNS & Domain: Domain names, subdomains, DNS zones, MX records, SPF, DMARC, NS...
Web & Applications: URLs...
Compliance: ensure your protection
DORA: Strengthens digital resilience in the financial sectors (banking, insurance).
NIS 2: Protects critical infrastructures (energy, healthcare, transportation).
Cyberscore: Assesses the security of digital services (websites, social media).
CaRE Program: Supports the cyber resilience of SMEs (industry, healthcare).
Advantages
Why Patrowl.io?
Zero False Positives
For qualified alerts
Simplicity
SaaS with no client-side maintenance or programming
0 setup
With a quick and simplified setup, averaging 30 minutes.
24/7/365
Including secure access (encryption and authentication via MFA or SSO).
100 %
Customer renewal rate in 2024.
Cyber Threat Intelligence as a service with Patrowl
Winners of the Cybersecurity Innovation Award at the Assises de la Cybersécurité in 2022 and 2023
Massive investment in R&D and AI
Estimated 287% client ROI
Features developed based on your needs
Certified "France Cyber Security"
Mentioned in Wavestone's radar

To go further
The Cyber Threat Intelligence (CTI) lifecycle
The CTI lifecycle is a structured process for proactively monitoring, analyzing and responding to threats. It follows an iterative approach to continuously reinforce the security posture.
Here are the key stages in the CTI lifecycle, along with the essential questions to ask at each phase:
1. Define priorities
Identify critical resources to be protected and prioritize each threat.
Which assets are essential to protect (e.g. systems, sensitive data, networks)?
What is the potential impact of cyber attacks on these assets?
What are the most likely threats based on the threat landscape?
What are the security objectives for these assets?
2. Collect information
Use appropriate tools to monitor and retrieve threat data.
What are reliable sources of threat information (e.g. hacker forums, threat feeds, security bulletins)?
What types of data do I need to collect? (Examples: indicators of compromise (IOCs), vulnerabilities, attacker tactics)
How can I automate the collection of this information to increase efficiency?
How can I ensure that the information collected is actionable intelligence and does not generate false positives?
3. Data processing
Organize collected data to make it usable.
How can I validate and clean up the data collected (e.g., eliminate false positives, correct errors)?
What data processing tools will help me organize the information? (Examples: SIEM, incident management systems)
How can I ensure that this data is ready for optimal analysis?
4. Threat analysis
Identify and prioritize vulnerabilities to determine their level of risk.
Which vulnerabilities are critical and require immediate attention (e.g. serious security breaches, misconfigurations)?
Which IOCs should be monitored as a priority?
What types of threats, such as Advanced Persistent Threats (APTs), have a high potential severity?
How can false positives and erroneous analyses be avoided?
Le SOC (Security Operations Center) et la Cyber Threat Intelligence
The SOC (Security Operations Center) is involved throughout the entire Cyber Threat Intelligence (CTI) lifecycle, but primarily during the analysis and incident response phases. From the collection phase, the SOC continuously monitors security events in real-time, processing and sorting alerts generated by the SIEM to identify real threats.
In the analysis phase, SOC analysts conduct in-depth investigations to understand the attackers' intentions, analyze vulnerabilities, and assess the impact of incidents. During the dissemination of results, the SOC communicates the findings to security teams and other stakeholders, then coordinates the necessary responses to mitigate the threat.
Finally, after each cycle, the SOC gathers feedback and provides recommendations to improve detection and response processes.

The SIEM (Security Information and Event Management) and Cyber Threat Intelligence
The SIEM (Security Information and Event Management) plays a crucial role from the start of the lifecycle, handling the collection, processing, and analysis of data.
It centralizes information from various sources within the organization, such as system logs, firewalls, and external security data, then correlates these events to identify patterns and indicators of compromise (IOCs).
The SIEM automates threat detection using predefined rules, enabling immediate alerts to the SOC about ongoing incidents.
By deeply analyzing this data, the SIEM helps prioritize threats and provides valuable insights for investigations, while generating reports to track the evolution of incidents and vulnerabilities over time.

FAQ
What types of Threat Intelligence are there?
There are several types of Cyber Threat Intelligence (CTI), each with a specific role in protecting systems and data:
Strategic Threat Intelligence:Focused on high-level information that influences the strategic decisions of decision makers. This includes long-term trends in the threat landscape and information on Advanced Persistent Threats (APT).
Tactical Threat Intelligence:Provides information on attackers' tactics, techniques and procedures (TTPs). This helps security professionals to better understand the methods used by cybercriminals to strengthen defenses.
Operational Threat Intelligence: details specific events and immediate threats requiring a rapid response. This includes information on current attacks and compromised IOCs.
Technical Threat Intelligence: Provides in-depth technical information, such as file hashes, malicious IP addresses and specific vulnerabilities. This type of intelligence is essential for technical analysts and vulnerability management teams.
What are the objectives of threat intelligence?
Centralize attack intelligence on an ongoing basis:
Identify attackers' objectives.
Determine what data is being targeted.
Identify indicators of compromise (IOCs), such as IP addresses and file hashes.
2. Analyze attackers and their strategies:
Understand their tactics, techniques and procedures (TTPs).
Identify the technologies and vulnerabilities exploited.
The main objective is to prevent cyber attacks by reducing your attack surface and improving your security posture.
What are the benefits of Cyber Threat Intelligence?
CTI is essential for proactive cybersecurity. It enables you to :
Reduce risks by detecting vulnerabilities before they are exploited.
Reduce the costs associated with cyber attacks, such as recovery costs and regulatory fines.
Improve security posture by reinforcing defenses based on identified threats and discovered vulnerabilities.





