Cyber threats can manifest in various forms, each posing unique risks to organizations. Some of the most prevalent types of cyber threats include:
Shadow IT – The use of unauthorized devices, applications, or services by employees without the knowledge or approval of the IT department. This creates an exposure to data leakage and other security risks as these assets may not be properly monitored or secured.
Data Leakage – The unintentional or malicious exposure of sensitive data to unauthorized individuals, often due to insufficient access controls or a lack of proper security measures.
Phishing Attacks – Cybercriminals use deceptive emails or websites to trick individuals into revealing sensitive information such as passwords, credit card numbers, or personal identifiers.
Counterfeiting – Attackers may create counterfeit websites, software, or services that closely resemble legitimate ones in order to steal sensitive data or launch other types of attacks, such as fraud or identity theft.
Ransomware – Malicious software that locks or encrypts an organization’s data and demands payment for decryption or restoration of access. Ransomware can cause severe operational disruption and data loss.
Man-in-the-Middle (MitM) Attacks – Cybercriminals intercept communications between two parties to steal or alter information, often exploiting unencrypted networks or insecure communication channels.
Denial-of-Service (DoS) Attacks – Attackers flood a network, server, or website with an overwhelming amount of traffic, making the targeted service unavailable to legitimate users. Distributed Denial-of-Service (DDoS) attacks are even more powerful and difficult to mitigate.
Malware – A broad category of malicious software, such as viruses, worms, and Trojans, designed to infiltrate, damage, or steal data from computers and networks. Malware can also be used to launch data breaches and disrupt business operations.
SQL Injection – A vulnerability in web applications where attackers insert malicious SQL code into input fields, enabling them to access or manipulate the database, often exposing sensitive user data.
Insider Threats – Threats originating from within an organization, either from malicious intent or careless actions by employees, contractors, or business partners. This can include unauthorized access to systems or data leakage.
Cryptojacking – Cybercriminals hijack a victim’s computing power to mine cryptocurrencies without their consent. This can lead to degraded system performance and loss of computing resources.
Advanced Persistent Threats (APTs) – Highly sophisticated, targeted attacks typically carried out by state-sponsored actors or well-funded criminal organizations. APTs are designed to infiltrate systems and remain undetected over a long period of time to steal sensitive data or disrupt operations.
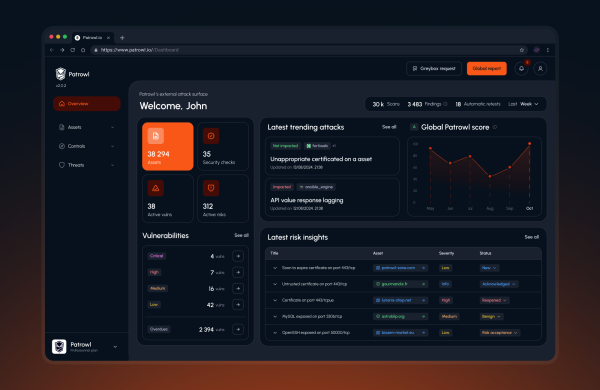
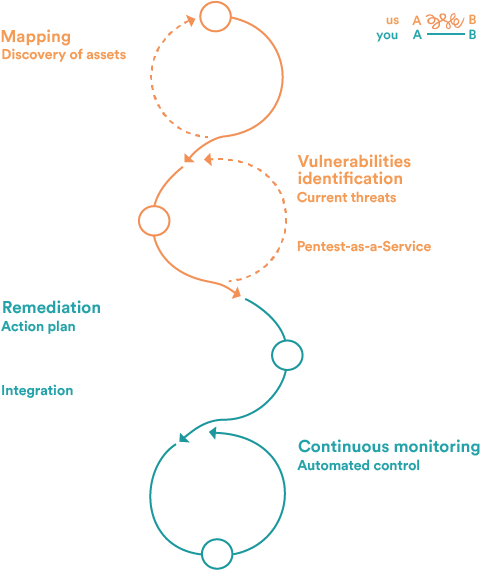
Shadow IT and Exposed Assets – As more devices and services are connected to the internet, organizations lose visibility into their attack surface, making it easier for threats to go unnoticed. Continuous monitoring is crucial to track and protect these assets from emerging vulnerabilities.
Counterfeit Services and Fraud – Cybercriminals often use counterfeit services to impersonate legitimate companies or platforms, leading to fraudulent transactions and security breaches.
Weak Encryption – Inadequate encryption or lack of encryption altogether can expose sensitive data to attackers, increasing the risk of data theft, data breaches, and privacy violations.
SQL Injection – This technique allows attackers to inject malicious code into an application's database, granting them access to confidential information and compromising the integrity of the system.
Lack of Visibility – Without effective continuous monitoring and automated vulnerability testing, organizations can lose track of the vulnerabilities in their systems and exposed assets, leaving them open to exploitation.
Risk of Attack Surface Expansion – As organizations grow and deploy new services, their attack surface expands. Regular vulnerability assessments and monitoring are necessary to minimize the risk of exposure and data leakage.
Advanced Malware – These attacks often bypass traditional defenses, making use of zero-day vulnerabilities or advanced obfuscation techniques to avoid detection.
Insufficient Remediation Plans – A key risk factor is the failure to implement a clear, prioritized remediation plan for addressing identified vulnerabilities, which could result in lasting damage to the organization’s security posture.