Platform
Cyber risk management for CISOs
As an Information Systems Security Officer (ISSO) or Chief Information Security Officer (CISO), you face a multitude of challenges in ensuring the security of your organization's digital assets.
The growth of cyber threats, vulnerability management, regulatory compliance and the need to demonstrate a return on cybersecurity investment are major issues.
Did you know?
36%
of CISOs rely on sufficient resources to ensure 24/7 cybersecurity coverage.
35%
use attack surface management techniques to measure the perimeter.
34%
use proven regulatory frameworks and standards
CISO missions

Prepare for threats: Adopt continuous monitoring strategies and assess threats to anticipate attacks.
Instill a culture of security: Raise employee awareness and organize training to promote secure practices at all levels.
Manage supplier risks: Audit third-party partners and impose security standards to limit the risk of leaks and interruptions.
Reinforce data confidentiality: Deploy data protection and minimization policies to guarantee confidentiality from the moment data is collected.
React to security incidents: Draw up an incident response plan to rapidly contain attacks and minimize their impact on the organization.
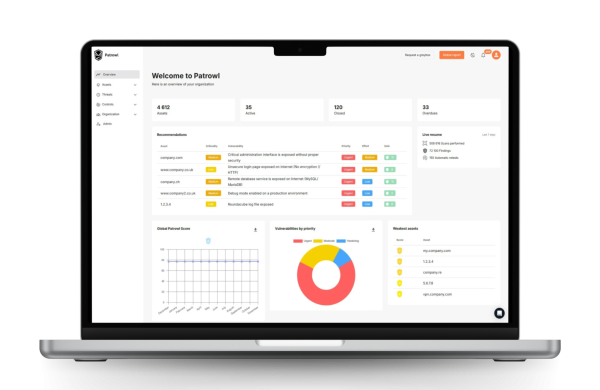
CISO & vulnerability management
Patrowl offers you a complete solution for Continuous Cyber Threat Exposure Management (CTEM).
Reduce risk: With proactive vulnerability identification, you can anticipate threats before they materialize.
Improve visibility: Advanced mapping (EASM) enables you to visualize your entire attack surface and identify assets exposed on the web.
Facilitate remediation: Benefit from a clear action plan and actionable recommendations for correcting vulnerabilities.
Increase efficiency: Alerts and notifications keep you informed of new vulnerabilities affecting your assets.






