Platform
Leader in offensive security
Offensive Security as a Service (OSaaS)
Patrowl protects everything your company exposes on the Internet with a unique approach: continuous vulnerability management combined with automated, expert-led hybrid pentesting.
Thanks to this combination, you can effectively secure your external attack surface and correct critical vulnerabilities before they are exploited.
Don't waste any more time
Your challenges
Too many complex, time-consuming and skill-intensive tools
Overworked and undersized teams
Time-consuming manual validations to secure your systems
With Patrowl :
Automate your defenses without prior expertise
Rapidly raise your level of cybersecurity
Reduce risk and save time
Our mission
To identify as many critical vulnerabilities as possible in record time, and help you correct them before they become entry points for attackers.
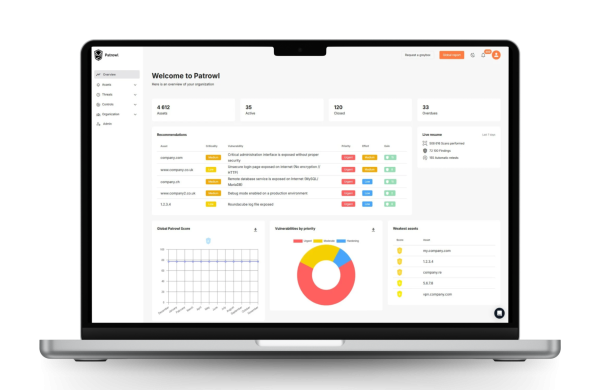
Patrowl is one unique product which does:
Continuous (re)discovery of all your Internet exposed assets, partially with our External Attack Surface Management (EASM)
Continuous identification of all your weaknesses and vulnerabilities with our continuous pentest (Continuous Automated Red Team / CART), our Pentest as a Service (PTaaS) and our realtime cyber threat monitoring
Easy remediation from our dashboard with prioritization and contextualization
Control of the remediation with the ability to retest with 1 single clic
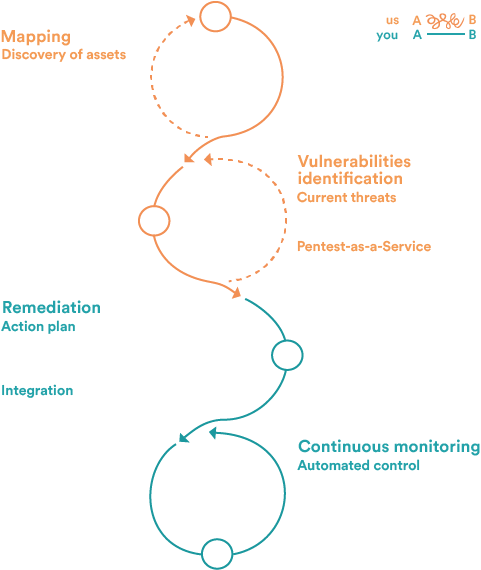
Combating cyberthreats with hyper-automation and the expertise of our slotters
Stay ahead of evolving threats and vulnerabilities with real-time alerts and prioritized remediation. Streamline cybersecurity with automation, reduce costs and maximize ROI by managing all your external assets on a single platform.
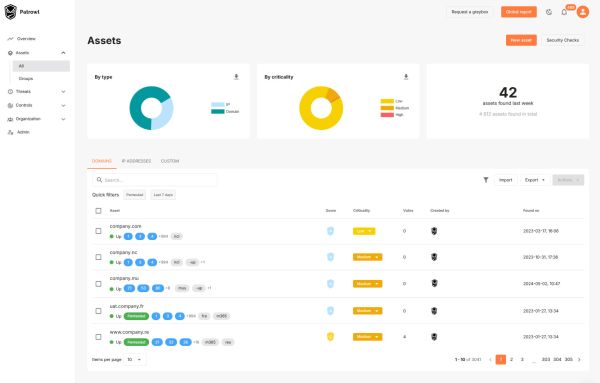
Mapping your attack surface (EASM)
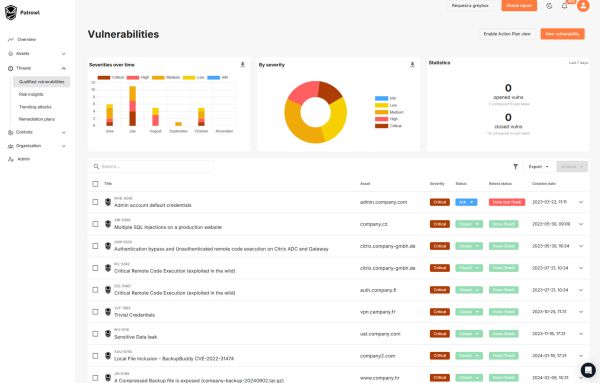
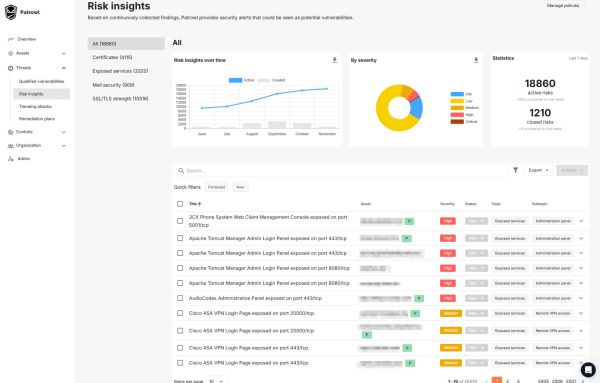
Risk qualification and prioritization & risk-based rating
Patrowl qualifies each vulnerability by assessing :
technical severity,
likelihood of actual exploitation,
the presence of public exploits or known attack techniques,
the level of exposure of the asset concerned.
This prioritization is based on relevant metrics and an automated scoring engine, adapted to your business context.

Automated, contextualized remediation plans

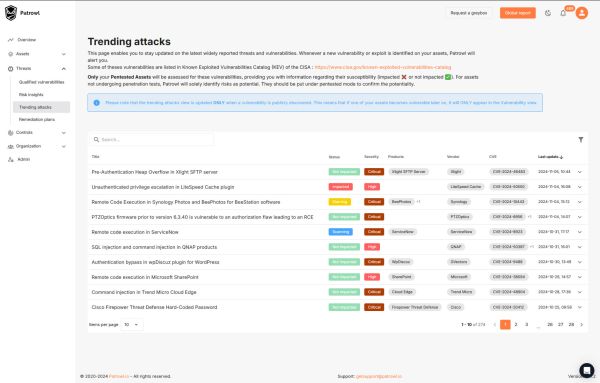
Continuous monitoring and qualified alerts
Patrowl monitors your assets in real time, notifying you only of qualified alerts (avoiding the “background noise” effect). You are informed only when necessary.






Your questions about OSaaS :
What is the meaning of security as a service?
Offensive Security as a Service (OSaaS) is a model where security experts provide proactive testing and vulnerability assessments, such as penetration testing, to identify and address security risks, helping organizations stay ahead of threats without in-house security teams.
What is OSEP in offensive security?
OSEP (Offensive Security Experienced Professional) is a certification from Offensive Security, focusing on advanced penetration testing and real-world cybersecurity skills.





