
Blog: Fortigate CVE-2023-27997 (XORtigate) in the eyes of the owl
Published on

Note that this means that if a software/hardware/operating system is not monitored by the MITRE, its vulnerabilities will not be referenced. This is also the case for vendors who do not communicate on their vulnerabilities (IBM on its mainframe, SAP on Hybris...).
CVEDetails allowed to make rankings, statistics, to have the history of all the products... and this for free.
Example :
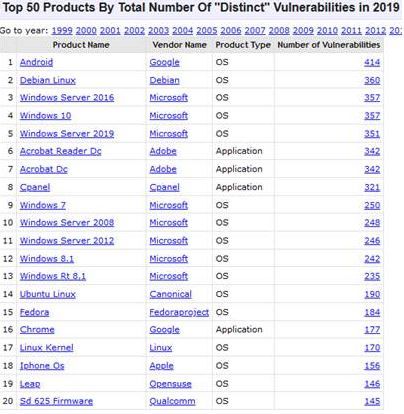
CVEDetails was maintained by Serkan Özkan, who decided to stop. It's sad. The history of CVEDetails was supposed to stay online, but will not be updated anymore.
Instead he recommends his other paid solution VulnIQ, which has a free but limited version (no info on exploits): https://free.vulniq.com
There are also other solutions like https://vuldb.com/
On our side, we have developed our own solution named PatrOwl Hears, which should be released very soon. On the other hand, as CVEDetails existed, we didn't plan to have statistics, graphs... but it could evolve 😉.