
Blog: Fortigate CVE-2023-27997 (XORtigate) in the eyes of the owl
Published on

SMBGhost, SMBleed, SMBLost, what an imagination for these vulnerability names 😉.
I remind the basic rules:
This vulnerability allows a memory leak without authentication, affecting SMBv3 (3.1.1 to be exact): https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1206
This vulnerability affects the latest versions of Windows 10 and Windows Server, if SMBv3 is enabled with compression.
The vulnerability has been discovered by ZecOps: https://blog.zecops.com/vulnerabilities/smbleedingghost-writeup-chaining-smbleed-cve-2020-1206-with-smbghost/
The demo code requires a writeable share and an account, but it also works without authentication as it works with almost all "SMB" messages.
Amusingly, the vulnerability is in the same decompression function (Srv2DecompressData) as the SMBGhost vulnerability from March 2020 (see "Security SMBGhost, Critical Vulnerability on SMBv3 and Quick SMB History / CVE-2020-0796"). This is quite surprising for a function that is barely 10 lines of effective code!
It is an integer overflow allowing to allocate a small memory area whose content can be retrieved, the memory bleed.
As it seems to be possible to partially control the location of the allocation and as SMB is executed by the Windows kernel, it is therefore possible to read part of the kernel memory and thus to retrieve keys, password digests of past or current sessions (unless Credential Guard is enabled), memory addresses...
This vulnerability allows remote code execution with authentication, affecting SMBv1, old version that should not be used anywhere anymore 😉: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1301
This vulnerability affects the latest version of Windows 10 and Windows Server, if SMBv1 is enabled.
The vulnerability was discovered by Nicolas Delhaye from AIRBUS, who wrote a full article on the subject: https://airbus-cyber-security.com/diving-into-the-smblost-vulnerability-cve-2020-1301/
It is an integer overflow generating an arbitrary write in memory with the particularity that the name of the targeted shared directory ends with "", like for example the "c:" share but more often local than remote.
The article presents an exploit code in Python 2 that you have to adapt a bit if you use Python 3. It generates a denial of service (crash) and to make it work, you have to follow the instructions of the article well (you feel the guy who had a little trouble😉).
My target does have the SMB port accessible:
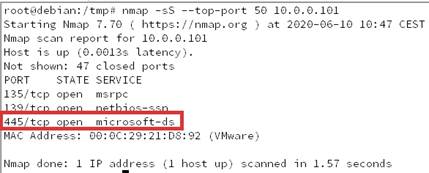
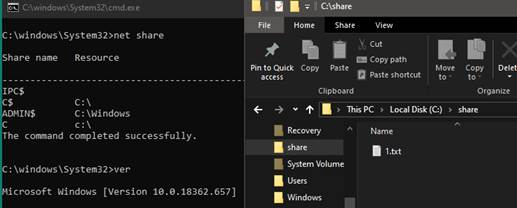
It is a Windows 10 with the test conditions:
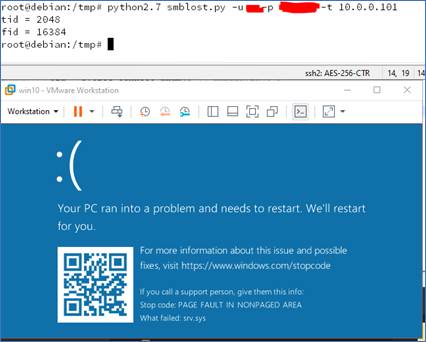
And it crashes well when I run the PoC:
This vulnerability has already been presented in March but I found interesting to present a complete exploitation code that has just been published on github: https://github.com/chompie1337/SMBGhost_RCE_PoC/blob/master/README.md
I'm not going to repeat the usual "partition", "update" and "don't expose SMB", so I'll limit myself to a simple "have a precise knowledge of your information system with the exposure and criticality of each component in order to be able to make a quick analysis when this kind of vulnerability comes out".
Good luck all the same 😉.