
Blog: We Wanted to Talk About Cyberattacks During the Olympics, but We Have Nothing to Say
Author: Vlad
Published on
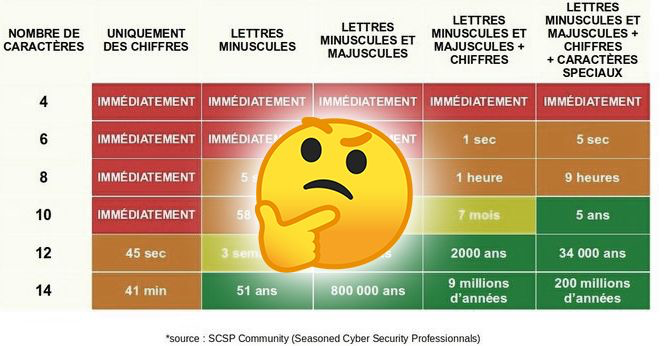
I recently saw a tweet from the Vosges Gendarmerie about the strength of passwords containing this picture:
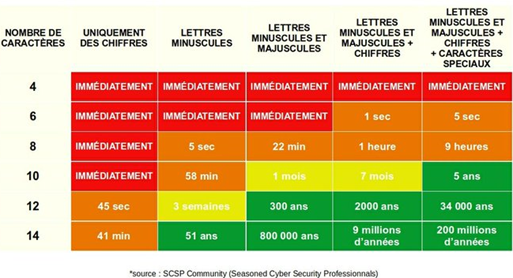
Although very interesting and giving a good idea of how complex a password should be, this information, without context or explanation, is a bit misleading in giving the impression that a password of, say 12 characters, is sufficient.
Unfortunately it's much more complex (as it often is 😉 ).
If you attack an account on its password, there are two categories of attacks:
This has already been covered by the presentation I gave at OSSIR in May 2019 as well as the blog post "Breaking password digests... without violence", but here are some reminders and additions about these attacks.
To perform an "Offline" attack, you need something that allows you to retrieve the user's password. In general, this something is a hash of the password. It is usually a non-reversible transformation.
Sometimes it is performed on the password, together with a salt. It is an additional element, unique for the password, and allowing to prevent any pre-computation attack (the famous Rainbow Table) to find the password, from the condensate.
It can also be an intermediate pre-computation as for WPA2 with PMKID, a signature... but to make it simple, let's talk about condensates, because the breaking techniques are finally similar.
These condensates can come from several sources:
There are two main families :
This is the simplest and often the longest technique, because it consists in taking all the possible passwords, generating the condensate with the same algorithm as the one of the condensate we are trying to "break" and seeing if the resulting condensates are the same (which means that the password is the right one, with the rather unlikely collisions on passwords).
And this is where the above table comes in with several remarks:
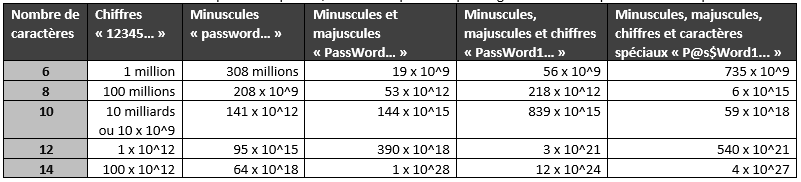
Computation time on my laptop for the SHA-2 256 bits condensation algorithm, used by many websites :
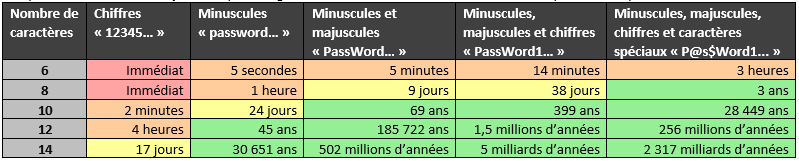
Computing time on our dedicated breaking machine for the 256-bit SHA-2 condensate algorithm:
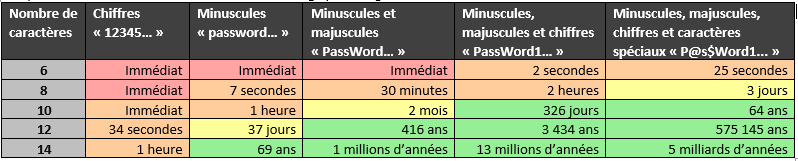
Computation time on my laptop for the NTLM condensation algorithm, used by Microsoft to store user passwords:
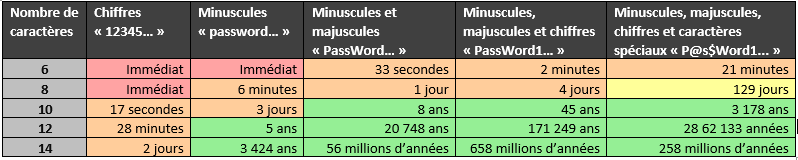
Computation time on our dedicated breaking machine for the NTLM condensate algorithm:
Overall, the results are quite similar between my last picture and the one mentioned in the introduction. Moreover, I kept the philosophy of the colors but between immediate and less than an hour, for me there is no difference.
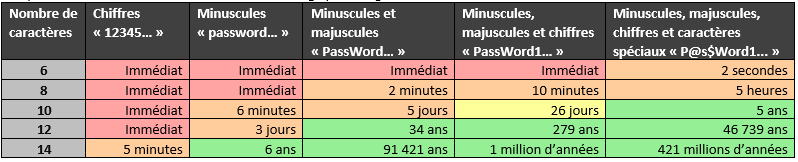
You also have these reference values from RandoriSec which are quite accurate (on another condensate algorithm):
As it is complicated to find long passwords, there are several techniques that I have already detailed (cf. "Breaking password condensates... without violence") with the use of masks, i.e. limiting the space of possibilities (types of characters) for certain positions, such as, for example, all words (existing or not) capitalized of a certain length and ending with two digits (e.g.: Sunday20! )
To further reduce the range of possibilities, the use of dictionaries completed with derivation rules remains very effective, mainly because many people use common words for their passwords, completed with special but classic characters and always positioned in the same place.
Moreover, following the numerous data leaks that have taken place and the diffusion of their condensed databases or even passwords, most attackers have dictionaries containing many real passwords, improving the breaking, here again, I refer you to the various articles cited.
This is a completely different subject and the table in the introduction may be confusing.
When we talk about "online" attack it means that we try passwords directly on the application, the website, the service... The attacker is therefore dependent on several limits:
Here are the different attacks that can be performed.
It is simply a matter of testing all possible passwords but rarely possible because of the limits mentioned above. With a response time of 300ms (which is already good) testing just 1,000 passwords already takes 5 minutes without parallelizing and if there is no limit.
Here again, as for the "offline" attacks, it is a question of testing the contents of dictionaries of passwords, with or without derivation rules, but here again, this attack is dependent on the limits mentioned above.
Exhaustive attack on test services
Sometimes, test services, development services... do not have some of the limitations described above and therefore allow to test a large number of passwords quickly. This was the case in 2016 for the "beta.facebook.com" platform.
This is the most classic technique: I find a data leak on site A and try the password associated with your account on site B. If you used the same password, too bad 😉.
This is mainly about testing few passwords but on a large number of users, so as not to be dependent on the limitations mentioned above. Several tools allow to automate this attack like :
Each tool has its advantages and disadvantages. They require an account list, passwords and a specific configuration for the targeted site:
I won't go into detail about these attacks which are often related to problems with the implementation of cryptography which is not done in constant time, but there are other techniques to get information about the password, leading in some cases to the ability to retrieve it.
I'm also not going to detail here all the techniques of session token prediction, token decryption... that's not the topic here 😉.
Here are some comments acting as conclusions, mostly related to the responses on the Vosges gendarmerie tweets.
Going back to the gendarmerie board and my introductory example, if a 12-character password is in a dictionary, then it's easy to break.
Just as a 9-character password can be difficult to break, if it is really complex (with a high entropy). So everything will depend on the information available to the attacker and the context.
So with "CM#Apollon1980", I am fine. On the other hand, forget about "ilovecats"
No, not if this password is in a dictionary and thanks for the idea, I'm adding it to my own dictionaries (at least the "CM#Apollon" because the year will be added by my derivation rules)
Not too much, it's often useless to "break" a password in 2020. Fighting against reuse is more important.
Yes yes yes!
The ideal is to use two-factor authentication: password + another authentication method.
Re-yes yes yes!
Hello @AXAFrance, the passwords of your customer area can be cracked "immediately". We, customers, hope that you will correct this.
No, an attacker won't be able to guess your password and authenticate for you on Axa or Facebook in 2 minutes, even if your password is 8 lowercase and uppercase (unless he already has your password).
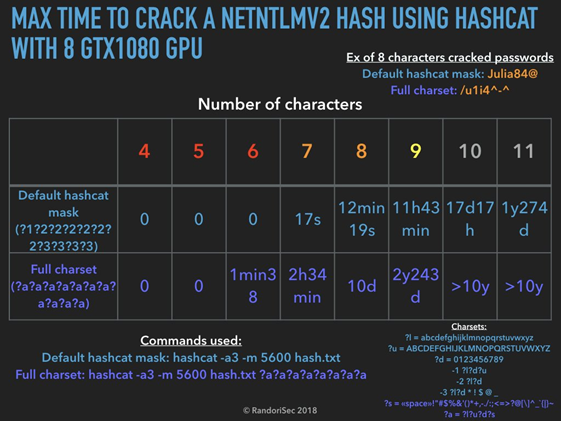
But Kevin Mitnick shows that you can break a complex password in a few seconds
Here is Mitnick's video showing how to break a complex password in less than a minute: https://www.youtube.com/watch?v=46ODE0bot1I&feature=youtu.be
It generates a password that looks strong but in reality it is not, then it uses the hashcat tool with a dictionary (not provided) and derivation rules (not provided).
This password is written in "leet speak", that is to say by replacing some characters by numbers (cf. wikipedia), a known technique and the hashcat tool embeds adapted derivation rules allowing to transform, for example, "password" in "p4ssw0rd". Then, as the dictionary and the derivation rules are not provided, it is impossible to know if this password (at least partially) is not already in its dictionary. The same is true for the derivation rules which are perhaps specifically adapted to this demonstration 😉.
Small additional interesting thing, it is easy to have different passwords on each sites. 1 - With password manager, 2 - By adding the site name to a basic password. So, for the second technique, it is only useful in a particular case
And no, using the same password with the site name is not a good idea. If an attacker looks at your case manually, it will be obvious for him to find your other passwords.
There are some security companies in France that will open 16 char/num/min/MAJ/specials in 15 minutes. And they (the judicial police) have forensic means to dispense with taking care of the password.
And no, the tools mentioned (here Cellebrite) mainly use vulnerabilities (or protection bypass techniques) to get into the devices and most often require physical access (I'm not going to talk about iCloud attack tools like Elcomsoft's here).
The best recommendation is to have a password vault (Keepass, Bitwarden, Dashlane...) with complex (randomly generated) and unique passwords per site/service, combined with a strong two-factor authentication.

Blog: We Wanted to Talk About Cyberattacks During the Olympics, but We Have Nothing to Say

Patrowl Raises €11m in Series A Funding: Continuous Protection of Internet Exposed Assets

Blog: RegreSSHion, critical vulnerability on OpenSSH CVE-2024-6387