
Blog: Fortigate CVE-2023-27997 (XORtigate) in the eyes of the owl
Published on

At the end of last year, the attack on the supervision tools editor SolarWinds made a lot of noise.
A publisher of network monitoring and management software, SolarWinds publishes Orion in particular, which is sold directly or integrated with other products and even sometimes deployed by remote maintainers without customers being aware of it.
In late 2019, SolarWinds was hacked and attackers added a backdoor to the Orion tool's source code. The tool was then deployed to tens of thousands of businesses and government agencies in a simple update.
This is a "supply chain attack", i.e. the compromise of a subcontractor to compromise another target(s). The case is sometimes called Solorigate or Sunburn and the attackers are called Dark Halo, UNC2452 or even Stellar Particle according to the companies that have worked on the subject.
What makes the attack so special are the precautions taken by the attackers, the very long duration of the attack and the accumulation of known, but particularly well mastered offensive techniques.
The attack lasted more than a year before one of SolarWinds' customers finally discovered the attack, due to the attackers' lack of discretion (overconfidence?).
Here is a diagram showing the main stages of the attack:
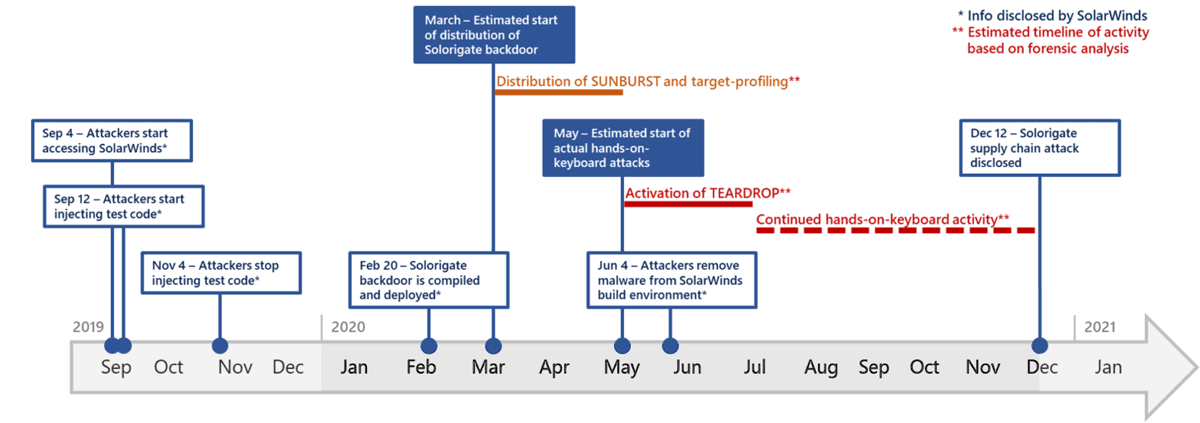
As the hacked agencies and companies are mainly American, Russia is pointed at.
For more details, I really recommend you to listen to the dedicated NoLimitSecurity episode, because the story is very interesting and contains many gems: https://www.nolimitsecu.fr/solarwinds/
Centreon is a French network monitoring solution, like Orion from SolarWinds. Published by the eponymous company, it is the solution that had been implemented by the teams of the outsourcing department that I had created in a former life. Based at first on Nagios and then on its own monitoring engine, Centreon is open, very modular, easy to use, allows to dedicate collectors per perimeter or customer... it is, functionally, an excellent solution 👍.
On the security side, it's more questionable with several vulnerabilities including remote takeovers (2 remote code executions identified in 2015, 4 SQL injections in 2018), fortunately patched.
Like Orion, Centreon was used to compromise corporate networks, mostly French, with a slightly different modus operandi than SolarWinds: the compromised versions were exposed to the internet, would be versions from 2015, not updated since and compromised from 2017.
The ANSSI has published an excellent analysis detailing the attackers' modus operandi: https://www.cert.ssi.gouv.fr/cti/CERTFR-2021-CTI-004/
The first compromises identified date back to 2017 and the last ones to... 2020. The attackers used one or more Centreon vulnerabilities to drop a backdoor in the form of a "web shell", i.e. a tool allowing the attacker to have a nice web interface in order to progress in the compromise: download content, run programs, rotate...
The "web shell" is P.A.S (acrynomye of PHP web shell) by Yaroslav Vladimirovich Pantchenko (son of Vladimir 😉), complete and quite discreet because it consists of a single PHP file, encrypted. It was generously made available on the author's site, which has since removed it.
Here is an excerpt from the ANSSI report presenting the interface of PAS (sometimes also called "Fobushell"):
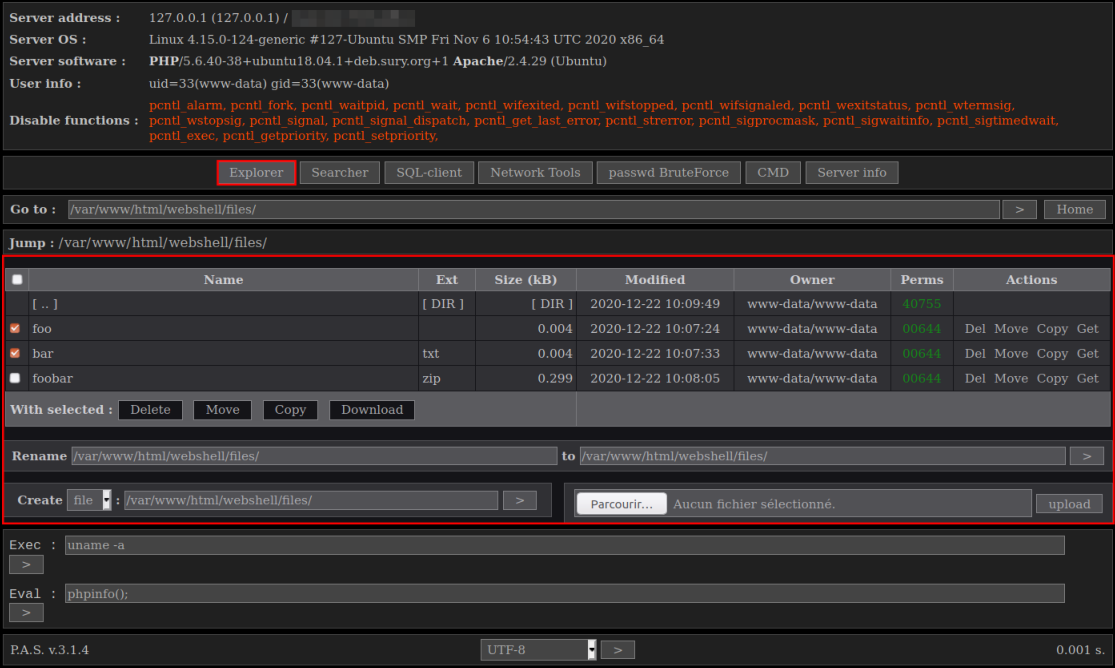
In its report, the ANSSI has made the effort to provide a number of indicators of compromise (IoC) and signatures, allowing to search for traces of attackers in its information system. Moreover, one person has even created an Ansible playbook to perform these searches: https://gist.github.com/humpalum/ce68317df2b740217ff2940f7479780b
Like any publication, it is criticized "haters gonna hate" :
Criticism in particular on the use of regular expressions, greedy in CPU resources, while it would be possible to optimize:
<< Detection rule No1 - if you can avoid a regular expression, then avoid it>>
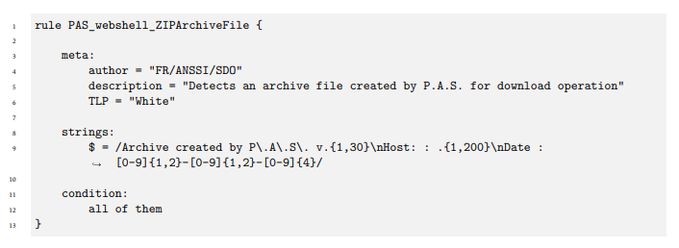
Criticism completed by what I hope is humor 😉 :

The fact that the ANSSI rules use "private" rules is also commented on, as making the content less clear, but I guess this comes from the fact that originally these rules were not meant to be published publicly :
<< #YARA tipp: Although the concept looks interesting, don't use "private" rules. They make it more difficult to handle and process rules and often - contrary to expectations - don't create a cleaner structure>>
https://twitter.com/cyb3rops/status/1361600018906505220
Regarding the attackers, the ANSSI has identified technical and operational similarities with Sandworm, a name given to a group supposedly linked to Russian intelligence and known for Industroyer (https://www.silicon.fr/sandworm-notpetya-industroyer-france-361796.html), an operation that successfully targeted Ukrainian power plants in 2016, as well as potentially NotPetya.
But in France, we do not attribute attacks to countries, we impute 😉.
As a result, the ANSSI report does not name any countries, yet on the specialized press side, Wired names Russia from the first line:
"The Russian military hackers known as Sandworm, responsible for everything from blackouts in Ukraine to NotPetya, the most destructive malware in history, don’t have a reputation for discretion. But a French security agency now warns that hackers with tools and techniques it links to Sandworm have stealthily hacked targets in that country by exploiting an IT monitoring tool called Centreon—and appear to have gotten away with it undetected for as long as three years.""
France Ties Russia’s Sandworm to a Multiyear Hacking Spree A French security agency warns that the destructively minded group has exploited an IT monitoring tool from Centreon. WIREDAndy Greenberg

Guillaume Poupard, the director of ANSSI, still commented on the attack and described it as <<😾Very unfriendly targeting and irresponsable❗️>> :
Guillaume Poupard on LinkedIn: Sandworm targetting Centreon | 11 comments 😾Very unfriendly targeting and irresponsable❗️👉 https://lnkd.in/dgx4TDV... 11 comments on LinkedIn LinkedIn58 Posts
I'll let you read the subtext 😉.
Following the ANSSI publication, Centreon communicated but focusing on the "web shell", describing it as a third-party module, developed by a third-party operator: <<The security breach does not concern a commercialized version of Centreon software ... an additional module developed by a third-party operator>>. They continue with <<We don't know what this module is, but it is absent from the codes and platforms produced by Centreon and the line of code on which it comes to operate has been absent from Centreon solutions since 2015 ... wild change >>. Uh yes... how to say... it is the attackers who dropped their backdoor, it is happy what "module" is not provided with Centreon 😉.
Cyberattack revealed in France: the Centreon company defends itself The mystery surrounding the cyberattack in France reported Monday by the French Information Systems Security Agency (Anssi) thickened Tuesday, with the targeted company Centreon blaming a third-party developer and its main customers remaining mum about potential impacts. 24matins.frBy 24matins.fr with AFP,
I guess they read the report diagonally, did not understand the technical aspects described and felt attacked. This is their clumsy way of rehabilitating themselves so the problem comes from the companies that used Centreon, without updating it for years and exposing it to the internet: the winning combo of compromise 💥!
The idea of compromising monitoring solutions, having access to the whole information system, is not new but it has just been exploited again for a campaign targeting this time Centreon.
Since the attack predates SolarWinds, could it have been a preparation? An opportunistic attack having given the idea to the attackers to attack a type of software? Who knows 🤔... Pure "putaclic" speculation and without the slightest basis from me 😂.
More software exposed on the internet and not updated...
Think of having up-to-date repositories, regularly map your information systems, make sure to update as a priority the components exposed on non-secure networks, as the Internet is and avoid exposing sensitive components directly on the Internet.
Let's finish on a touch of humor: << In July 2007, the Oreon software changes its name to Centreon due to a name conflict with Orion (monitoring software published by SolarWinds).>> https://fr.wikipedia.org/wiki/Centreon , the circle is complete 😎.