
What? Patrowl doesn’t report all your vulnerabilities?!
Author: Éliora
Published on

Yes, and we stand by it: Patrowl will not report all identified vulnerabilities. Why? Because not all vulnerabilities represent real dangers. Some may be: false positives, non-exploitable, or merely compliance issues that do not require immediate action.
It’s the opposite of a false negative. That’s it. You’re welcome :)
More seriously, a false positive is a result identified as relevant based on selection criteria, which seems correct but is actually wrong. For example, in cybersecurity, it could be legitimate and harmless software being flagged as malware by an antivirus. It could also be an alert for addressing a vulnerability that isn’t one, which is the subject of this article.
Imagine the following scenario: you receive this vulnerability alert concerning a website.
“AWS Access Key secret leak. An attacker could gain unauthorized access to your Cloud environment to steal data, alter configurations, and deploy malicious resources. The attacker could also maintain persistence on your systems, disable your services, steal data, and carry out illicit activities like cryptocurrency mining.”
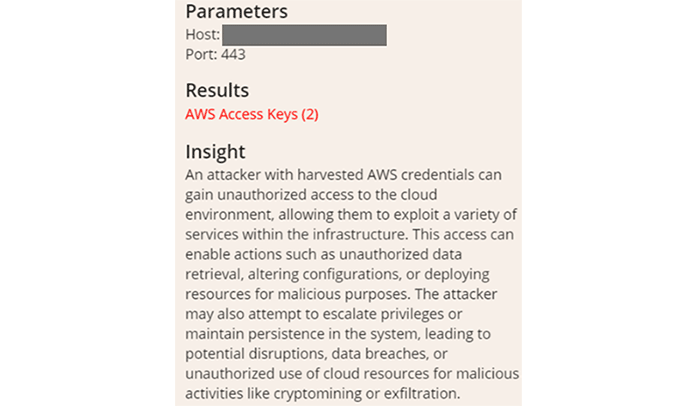
All alarms are flashing red, immediate intervention is required!
In reality, this alert concerns a public AWS access token, available to everyone, which provides access to public data. This is a normal and documented feature of AWS. You can store public images and public documents on AWS S3 storage spaces. To access these, the source code of your website must specify a token that lets AWS know where the document is located:
https://docs.aws.amazon.com/AmazonS3/latest/API/sigv4-query-string-auth.html.
So, nothing critical here—just a false positive.
When teams receive alerts about false positives, they must investigate to determine whether the threat is real or not. This results in a loss of time in an already time-constrained domain and mobilizes your teams on a non-priority subject.
In a cybersecurity ecosystem where false positives are increasingly frequent, experts can become desensitized to alerts—a phenomenon known as alert fatigue. Over time, this can lead to neglecting genuine threats, thereby increasing the risk of missing them.
IT teams rely on cybersecurity tools to provide precise and actionable information. If a tool constantly signals false positives, its effectiveness may be doubted, leading to disengagement from its use. Team feedback may quickly turn into: "This tool doesn’t work; there’s no point in using it."
False positives can trigger unnecessary security measures, such as account blocking or network isolations, rendering systems unavailable.
At Patrowl, we adhere to a zero false positives policy: a cybersecurity solution must be a reliable ally and not a source of confusion. All vulnerabilities reported by our platform are qualified, contextualized, and prioritized to ensure not only greater efficiency but also complete user trust in the solution.
Patrowl helps cybersecurity teams stay ahead of attackers. Focus on your real missions without getting lost in unnecessary signals!

What? Patrowl doesn’t report all your vulnerabilities?!

Blog: We Wanted to Talk About Cyberattacks During the Olympics, but We Have Nothing to Say

Patrowl Raises €11m in Series A Funding: Continuous Protection of Internet Exposed Assets