
Blog: We Wanted to Talk About Cyberattacks During the Olympics, but We Have Nothing to Say
Author: Vlad
Published on

Hello everyone,
Microsoft has published yesterday its security bulletin concerning its operating systems.
This one has in particular that two vulnerabilities are particularly critical:
This is a buffer overflow vulnerability allowing to execute code remotely, without authentication (it's ICMP 😉 ) on a target and to take control of it.
It is therefore particularly important to update, or at least block ICMPv6 on the local firewall or network firewalls. In cases I have tested, some firewalls with poor ICMPv6 support let these packets through, rendering them inoperable.
Microsoft's internal RedTeam has a working private PoC so I assume other teams also have working exploit code as the McAfee article is quite detailed and with the patch out, it has already been analyzed to understand its behavior.
Related articles:
This is a vulnerability affecting the SharePoint web agreement management software and allowing to take control of a server remotely but after authentication.
It is important to update because an exploit code has been published yesterday:
It should be noted that many other vulnerabilities are also quite critical like :
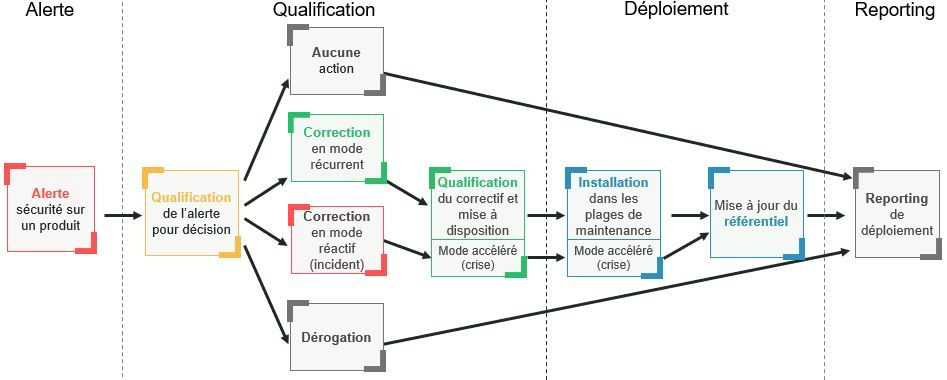
Otherwise, more simply: you apply these updates everywhere in a hurry 😉.

Blog: We Wanted to Talk About Cyberattacks During the Olympics, but We Have Nothing to Say

Patrowl Raises €11m in Series A Funding: Continuous Protection of Internet Exposed Assets

Blog: RegreSSHion, critical vulnerability on OpenSSH CVE-2024-6387